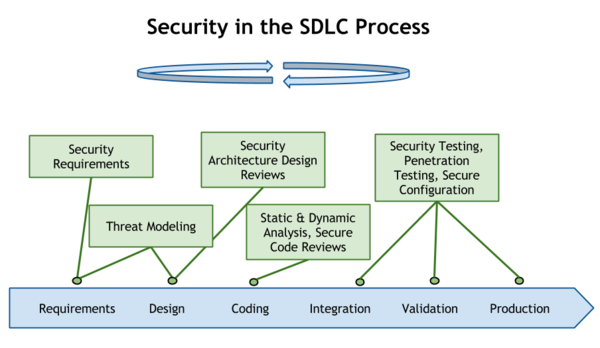
A secure sdlc with static source code analysis tools Secure software development lifecycle (s-sdlc) What is sdlc software development life cycle ample websol secure sdlc process diagram
Secure SDLC: A Look at the Secure Software Development Life Cycle
Phases of simple and secure process sdlc Secure software development life cycle (sdlc) introduction Secure system development life cycle (secsdlc)
Secure sdlc: a look at the secure software development life cycle
Secure sdlc: common phases and list of tasksBest practices for a secure software development life cycle How you should approach the secure development lifecycleSdlc development secure application security process modern defenses should talk could let fit into according.
Sdlc dzoneSecure sdlc processes. incorporating security into the sdlc… Sdlc overview: models & methodologiesSecure sdlc: a look at the secure software development life cycle.

Phases of software development life cycle with diagram
Secure sdlc should development phase lifecycle approach website considerations implementing account take into when some correspond followsSdlc processes How to achieve application security with a secure software developmentSoftware development life cycle sdlc phases of sdlc mechomotive.
Best practices to secure your sdlc process5 phases of secure sdlc Secure sdlc phase security phases requirements requirement tasks common list dzone software each team involved identify write downDevelopment sdlc software secure security phase concept structural ensuring desde guardado integrate every standards cycle life.

Pin en hack2secure
Secure sdlc policy templateSix best practices for security testing in the sdlc Secure software development life cycle (secure sdlc)Adaptive secure sdlc process.
Sdlc principles secure practices experts exchange process figureBuilding a secure sdlc for web applications What is a secure sdlc?Sdlc stages software lifecycle suitable.
Implementing secure sdlc: a step-by-step guide
Sdlc phases a..k.a. software development life cycle processSdlc security testing practices development software cycle life application resilience coding six cybersecurity phases phase cyber web solutions will require Case studiesHow to build a secure sdlc—the right way.
Integrating security into the sdlcSdlc secure security assessment coding application checkmarx testing framework lasting ways Sdlc lifecycle agile tenendoSecure software development life cycle processes (sdlc) innuy.

Secure application development and modern defenses
Secure sdlc phases and practices: things to considerSecure sdlc principles and practices .
.